TCP/IP is a typical communications protocol used in networked computers. It stands for Transmission Control Protocol/Internet Protocol.
Establishing effective communication between computers across diverse networks is crucial for data transfer. The TCP/IP suite plays a fundamental role in managing these communications. It breaks down information into packets, ensures their error-free transmission, and reassembles them at the destination.
Initially developed for the ARPANET, the precursor to the modern internet, TCP/IP has become the backbone of the current internet and is essential for tasks like web browsing and email transmission. Understanding TCP/IP is vital for IT professionals and anyone involved in digital communications. Its design is instrumental in facilitating the connection of different devices and systems, ensuring compatibility and information security across the globe.
The Essence Of Communication Protocols
Communication protocols are sets of rules that help electronic devices to communicate. These rules are vital. Without them, our phones, computers, and the internet couldn’t work together.
Core Functions Of Protocols
Protocols make sure data moves correctly from one point to another. They handle errors, setup connections, and transfer data.
- Error checking: They spot mistakes in data.
- Data encapsulation: This wraps data in a certain format before sending it.
- Addressing: They find the right path for data.
- Synchronization: They keep data transmission steady.
The Role In Networking
Protocols are the backbone of networking. Without them, devices couldn’t share data.
Networks like the internet rely on protocols to work properly.
They follow set steps for devices to connect and communicate.
| Level | Function |
|---|---|
| Application | Software communication |
| Transport | Data transfer control |
| Network | Addressing and routing |
Exploring Common Protocols
In the realm of digital communication, certain rules ensure data travels smoothly. These rules, known as protocols, are essential for exchanging information between devices. Let’s dive into some typical communication protocols that keep our digital world spinning.
TCP/IP For Internet Success
Transmission Control Protocol/Internet Protocol (TCP/IP) is the backbone of the Internet. Every email, tweet, or web page visit relies on this duo for successful data delivery. Here’s why TCP/IP is crucial:
- Reliable: It ensures complete data transfer, even across vast networks.
- Flexible: It works well with various devices and networks.
- Efficient: It optimizes data flow to avoid congestion.
HTTP And The Web
When browsing the web, you’re using the Hypertext Transfer Protocol (HTTP). HTTP is the messenger of the web, carrying requests from your browser to the server and delivering the web pages back to you.
| HTTP Feature | Description |
|---|---|
| Stateless: | Servers do not retain user data between requests. |
| Secure (HTTPS): | Adds encryption via SSL/TLS for safety. |
| Flexible: | Handles various content types like HTML, images, and videos. |
Imagine a reliable postal service. Now apply that to the digital world. You get protocols like TCP/IP and HTTP. They ensure your data ‘letters’ arrive intact and secure, no matter the distance.
Email Transportation
Let’s dive into how emails find their way to our inboxes. Email transportation involves several steps and key protocols. Protocols are like rules that everyone follows to understand each other. Email transportation uses these rules to send and receive messages.
Smtp: The Email Sender
First up is SMTP, which stands for Simple Mail Transfer Protocol. SMTP is like the postman for emails. When you hit send, SMTP takes your message and delivers it to the recipient’s server.
IMAP And POP3
IMAP stands for Internet Message Access Protocol. POP3 stands for Post Office Protocol version 3. These are like the keys to a mailbox.
- IMAP lets you read your emails without actually taking them out of the mailbox. It’s like checking your mail without taking it home.
- POP3 lets you take the mail out, and it’s only on your device after that.
Below is a quick comparison:
| Protocol | Function |
|---|---|
| SMTP | Sends emails to server |
| IMAP | Keeps emails on server |
| POP3 | Downloads emails |
Secure Data Transmission
In the digital world, secure data transmission is a must-have. With risks like data breaches and eavesdropping, protection protocols are vital. These protocols keep private data safe. They are like secret codes that only the sender and receiver can understand. Below are key protocols that help in keeping our online communications safe.
SSL/TLS For Encryption
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols for encryption. Encryption makes data unreadable to others. These protocols secure web browsers and servers. They create a secure tunnel for data. Think of this as a protective pipe where no one can see inside. Sites with ‘HTTPS’ use these protocols. Here’s why SSL/TLS are important:
- Encrypts sensitive information.
- Prevents data tampering during transmission.
- Builds trust with visitors through security badges.
- Meets compliance standards for online security.
Ssh For Secure Shell Access
SSH (Secure Shell) is a protocol for secure access. It lets users remotely connect to another computer securely. It provides a secure channel in an insecure network. Here is what SSH does for secure data transmission:
- Encrypts the entire session.
- Guards against attacks such as IP spoofing and packet sniffing.
- Allows for secure file transfers using SCP and SFTP.
- Uses public-key cryptography for authentication.
Protocols For File Transfer
In the digital world, moving files from one place to another is common. File transfer protocols make this possible. They are rules computers follow to transfer files. Different tasks need different protocols. Today, let us explore some typical protocols for transferring files efficiently and securely.
Ftp: Sharing Large Files
FTP, or File Transfer Protocol, is a go-to solution for sharing large files. Businesses and web developers often use FTP. It allows bulk file uploads and downloads. FTP works well for managing website files directly on a server.
- Simple: Easy-to-use for transferring large files.
- Accessible: Works with various FTP client software.
- Customizable: Allows permission settings for different users.
FTP requires a server and client software. Users enter their credentials to access files.
Sftp For Secure Transfers
SFTP, or Secure File Transfer Protocol, builds upon FTP. It adds a critical layer of security. SFTP encrypts data before sending over the internet. This encryption keeps files safe from unauthorized access.
- Encrypted transfer: Keeps files secure during transit.
- Uses SSH: Protects the login credentials.
- File management: Allows users to view, edit, and manage files securely.
For sensitive data, SFTP is preferred. It ensures that files reach their destination without interception.
Wireless Communication Standards
Imagine talking to someone far away without wires. That’s what wireless communication does. Like walkie-talkies, but much smarter. Your phone and computer use them every day. Now, let’s explore some typical protocols that make this magic happen.
Wi-fi Protocol Suite
Wi-Fi connects our devices to the internet without cables. It’s like an invisible thread linking your gadgets to the world. The Wi-Fi Protocol Suite is a set of rules. They ensure that devices speak a common language.
| Protocol | Frequency | Speed |
|---|---|---|
| 802.11b | 2.4 GHz | Up to 11 Mbps |
| 802.11g | 2.4 GHz | Up to 54 Mbps |
| 802.11n | 2.4/5 GHz | Up to 600 Mbps |
| 802.11ac | 5 GHz | Up to 1.3 Gbps |
Each version improves speed and range. So, devices work better and faster. Consider which one suits your needs best.
Bluetooth Communication
Bluetooth lets devices talk over short distances. It’s like a secret conversation between gadgets. Phones, speakers, and watches use it. It’s handy for sharing files and streaming music.
- It uses low energy, so your battery lasts longer.
- Personal Area Network (PAN): Connects devices close to you.
- Easy pairing: Just bring them close and connect.
Remember, Bluetooth versions matter too. Newer ones offer longer range and more speed. Always check these before pairing your devices.
Emerging Protocol Technologies
Today’s tech landscape is dynamic and ever-evolving. One area to watch is protocol technologies. Protocols are rules that devices follow to communicate. As technologies advance, so do these rules. Let’s dive into two exciting areas: IoT (Internet of Things) protocols and 5G network protocols.
IoT Protocols
IoT devices are everywhere! They make life easier and smarter. For smooth talk between these gadgets, special rules, or protocols, are vital. Here are a few:
- MQTT: A lightweight messaging system for small devices.
- CoAP: Enables devices to talk to each other using the web.
- Zigbee: A protocol for personal area networks, like home automation.
5G Network Protocols
Speed rules with the 5G! But it’s more than just fast internet. It’s a game changer. This next-gen network uses new protocols to make sure everything is quick and safe. Here’s a sneak peek:
| Protocol | Role |
|---|---|
| HTTP/2 | The backbone of web communication, now faster. |
| AMF | Helps manage the connections of mobile devices. |
| QUIC | Makes internet activities secure and speedy. |
Choosing The Right Protocol
Choosing the right communications protocol is crucial for your network’s efficiency and reliability. Protocols are the rules that allow devices to communicate across a network. Picking the correct one can mean the difference between smooth sailing and rough seas for your data.
Factors To Consider
When exploring communication protocols, a variety of factors come into play:
- Compatibility: Ensure the protocol aligns with your existing equipment and software.
- Function: Match the protocol’s capabilities to your specific needs.
- Security: Look for protocols with robust security features to protect your data.
- Scalability: Choose a protocol that can grow with your network’s expansion.
- Cost: Consider the financial impact, including licensing fees and hardware requirements.
Impact On Performance
The chosen protocol directly affects how well your network performs. Here’s how:
| Protocol Aspect | Impact on Network |
|---|---|
| Speed | High-speed protocols let information flow quicker. |
| Reliability | Reliable protocols ensure data reaches its destination. |
| Efficiency | Efficient protocols use less bandwidth, saving resources. |
High-speed, reliable, and efficient protocols create a smooth experience for users, handling more data with fewer errors.
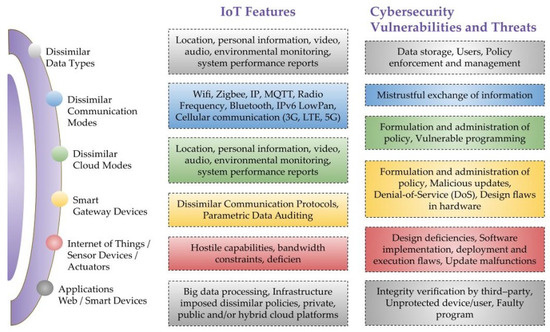
Credit: www.mdpi.com
Frequently Asked Questions For Which Of The Following Is A Typical Communications Protocol?
What Is A Communications Protocol?
A communications protocol is a system of rules that allow two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. It ensures data is transferred accurately and securely.
Why Are Protocols Important In Networking?
Protocols are crucial in networking as they establish the rules for data exchange, ensuring efficient, reliable, and secure communication between devices. Without them, consistent and coherent data transfer would be near impossible.
What Are The Typical Types Of Communication Protocols?
Typical communication protocols include TCP/IP for internet networking, HTTP for web traffic, FTP for file transfers, SMTP for email, and Bluetooth for short-range device connections, ensuring diverse and specialized data communications.
How Does TCP/IP Protocol Work?
TCP/IP protocol works by dividing data into packets, which are then sent across the network to the target device. TCP ensures packets arrive correctly, while IP handles the addressing and routing, ensuring the data takes the best path.
Conclusion
Understanding communication protocols is crucial for effective networking. They enable devices to exchange information smoothly. TCP/IP, HTTP, FTP, and SMTP stand out as typical examples. Each serves distinct purposes in the digital communication landscape. Remember, choosing the right protocol is key for optimal performance and security.












































Leave a Reply